


Technology and Computer Services (also known as TeC Services or TeCS) provides computing and communications infrastructure, services, support, and innovation for Citrus College's instructional, research, public service, and administrative programs.
If you are an employee or currently enrolled student and need assistance with technology issues, support may be reached by phone at (626) 857-4100 or ext. 4357 (HELP) from on-campus, via email at TeCSHelpDesk@citruscollege.edu, or by submitting a Student Account Issues online form.
The Vision Resource Center is a resource from the California Community College's Chancellor's Office. Access classes and sign up for training on my.citruscollege.edu and click on the blue "start" button. You can also find documentation, on-line training from SkillSoft and Lynda.com, and a place where you can create and interact with a learning community of your choosing.
Citrus College faculty and staff who are responsible for creating, selecting, or maintaining electronic content and applications are under obligation to ensure their content complies with the California Community College Accessibility Standard. Diablo Valley College has developed an online accessibility website that contains easy to use guides on the following topics: Defining online accessibility and why it is important
Accessible Word 2015 Documents PC and Mac
Accessible PowerPoint 2016 Presentations (PC and Mac)
Accessible PDF (Portable Document Format) Files
Accessible Audio and Video
Canvas Accessibility Resources Thank you to Carrie Million from Diablo Valley College for creating this content and allowing us to link to it.
Citrus College is a member of the Foundation for Community College Microsoft Campus Agreement. As a student or employee of Citrus College, you are eligible to purchase computer products at a discount, including but not limited to current versions of Microsoft and Adobe software, through College Buys from Foundation for California Community Colleges.
According to Merriam Webster, phishing is "the practice of tricking Internet users (as through the use of deceptive email messages or websites) into revealing personal or confidential information which can then be used illicitly."
If you are suspect a phishing email, you can forward it to badmail@citruscollege.edu and you can mark it as phishing when you use Outlook.
Posted January 29, 2024
Artificial intelligence (AI) has continued to make news on its ability to help in different industries. The article by Schlosser, explains how AI has helped in the phone fraud and spam industry. The article shows that there has been a decrease worldwide on phone scams, however, AI has helped scammers in making it more believable. The article explains that scammers can take a three-second clip of a person's voice and then the AI can use it as its own voice targeting family members or friends.
In recent history, the holidays have always had an increase scam but may be heightened due the global circumstances. AI seems to be giving threat actors a variety of new tools to apply in their campaigns. It will be important for individuals to continue to be watchful for these campaigns.
Here are some links for tips to protect yourself this holiday season:
At the start of the month, many colleagues noticed intermittent issues using Outlook or Office 365 online. Microsoft was quick to investigate technical difficulties and posted on their Twitter page @Outlook informing users. In Schappert's article, it is explained that an overseas hacktivist group caused the problems as a reaction to recent sanctions imposed by U.S. Secretary of State Antony Blinken.
The ongoing events are affecting both work and daily routines, especially as we become increasingly reliant on cloud technology. Although companies are improving their cloud environments to become more resilient, they still face challenges as highlighted in the article.
What can we do to reduce the impact?
Content courtesy of author Phil Hoffman of the SANS™ Institute OUCH! Newsletter
Phishing emails used to be easier to detect because they were generic messages sent out to millions of random people. Cyber attackers had no idea who would fall victim; they just knew the more emails they sent, the more people they could trick.
Today's cyber attackers are far more sophisticated. They now research their intended victims to create a more customized attack. Instead of sending out a phishing email to five million people, or appearing to be generic emails sent by corporations, they may send it to just five people and tailor the attack to appear to be sent from someone we know. Cyber attackers do this by:
Because cyber attackers are taking their time and researching their intended victims, it can be more difficult to spot these attacks. The good news is you can still spot them if you know what you are looking for. Ask yourself the following questions before taking action on a suspicious message:
If a message seems odd or suspicious, it may be an attack. If you want to confirm if an email or message is legitimate, one option is to call the individual or organization sending you the message with a trusted phone number.
Beware of fraudulent schemes seeking donations or other financial assistance related to the crisis in Ukraine.
According to the FBI, Criminal actors are taking advantage of the crisis in Ukraine by posing as Ukrainian entities needing humanitarian aid or developing fundraising efforts, including monetary and cryptocurrency donations.
Scammers similarly have used past crises as opportunities to target members of the public with fraudulent donation schemes.
Tips on how to protect yourself:
The Internal Revenue Service warns that the beginning of the new year is an opportune time for scammers to use e-mail, text messages and/or phone calls to defraud unsuspecting victims.
"With filing season underway, this is a prime period for identity thieves to hit people with realistic-looking emails and texts about their tax returns and refunds," said IRS Commissioner Chuck Rettig. "Watching out for these common scams can keep people from becoming victims of identity theft and protect their sensitive personal information that can be used to file tax returns and steal refunds."
Last year, there was an uptick in text messages that impersonated the IRS. These scams are sent to taxpayers' smartphones and have referenced COVID-19 and/or "stimulus payments." These messages often contain bogus links claiming to be IRS websites or other online tools. Other than IRS secure access, the IRS does not use text messages to discuss personal tax issues, such as those involving bills or refunds. The IRS also will not send taxpayers messages via social media platforms.
As a new tax season begins, the IRS reminds workers to watch out for claims of unemployment or other benefit payments for which they never applied. States have experienced a surge in fraudulent unemployment claims filed by organized crime rings using stolen identities. Criminals are using these stolen identities to fraudulently collect benefits. You may have been the victim of identity theft if you have received mail or an IRS Form 1099-G regarding benefits you were not expecting.
The IRS does not initiate contact with taxpayers by email to request personal or financial information. The IRS initiates most contacts through regular mail delivered by the United States Postal Service.
The IRS does not leave pre-recorded, urgent or threatening messages. In many variations of the phone scam, victims are told if they do not call back, a warrant will be issued for their arrest. Other verbal threats include law-enforcement agency intervention, deportation or revocation of licenses.
For more information on common IRS-related scams, and how to protect yourself, see https://www.irs.gov/newsroom/irs-warning-scammers-work-year-round-stay-vigilant
October has been designated as Cybersecurity Awareness Month. Now in its eighteenth year, Cybersecurity Awareness Month is a government and private sector partnership that raises awareness about cybersecurity and stresses the collective effort required to stop cybercrimes, online thefts and scams.
One of these scams has been dubbed the business email compromise (BEC) scam. This scam has been attempted several times at Citrus College. In a BEC scam, criminals send an email message that appears to come from a known source making a legitimate request, like in these examples:
Scammers use email or text messages to trick you into giving them your personal information. They may try to steal your passwords, account numbers, or Social Security numbers. If they get that information, they could gain access to your email, bank, or other accounts. Scammers launch thousands of phishing attacks like these every day — and they are often successful. The FBI's Internet Crime Complaint Center reported that people lost $57 million to phishing schemes in one year.
Scammers often update their tactics, but there are some signs that will help you recognize a phishing email or text message.
Phishing emails and text messages may look like they are from a company you know or trust. They may look like they are from a bank, a credit card company, a social networking site, an online payment website or app, or an online store.
Phishing emails and text messages often tell a story to trick you into clicking on a link or opening an attachment. They may
Here's a real-world example of a phishing email.
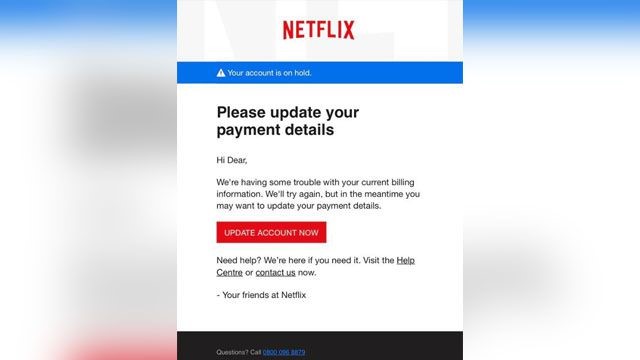
While, at a glance, this email might look real, it's not. The scammers who send emails like this one do not have anything to do with the companies they pretend to be. Phishing emails can have real consequences for people who give scammers their information.
Unfortunately, unethical criminals on the Internet are using the COVID-19 pandemic to trick people into giving up personal details, bank account and credit card information. The Federal Trade Commission (FTC) has helpful consumer advice at https://www.ftc.gov/coronavirus/scams-consumer-advice listing methods scammers use to take advantage of virus fears for financial gain.
The rollout of the COVID-19 vaccines has presented yet another opportunity for fraud. While vaccination details are getting worked out, here's what you can be sure of:
You can download an infographic with this information and advice on other coronavirus scams at https://www.ftc.gov/coronavirus/scams-consumer-advice
There has been a dramatic increase in the number of cybersecurity incidents reported since the start of the pandemic. On June 6, the University of California, San Francisco (UCSF) paid a ransom of $1.14 million to hackers to recover data from its School of Medicine that had been encrypted in a cyberattack. Similar attacks were carried out against Michigan State University and Columbia College, Chicago. In August, the University of Utah reported a payment of $457,000 to cybercriminals who held employee and student data for ransom.
Cybercriminals often take advantage of poor security practices by employees in order to conduct their activities. Keenan and Associates has provided Citrus College with a series of online training courses that can improve your security awareness. Help keep the IT resources and sensitive data at the college safe by taking one (or all) of the following courses, available on the training calendar:
Cybersecurity Overview: This introductory course provides an overview of cybercrime and cybersecurity, including the basics of cybersecurity along with the effects of cybercrime, the types of cyber threats and how users are susceptible.
Browser Security Basics: This course provides all staff members with an overview of browser security and ways to browse the web safely. Topics include: the types of browser threats, the basics of browser security and safe browsing practices.
Password Security Basics: This course provides an overview of password security and management, including the basic principles of password security, the elements of a strong password, and strategies of how to create and maintain passwords.
Email and Messaging Safety: This course provides an overview of cybercrime via email, and how to employ safe email and messaging practices to avoid and help prevent cyber threats, attempts at fraud and identity theft.
Protection Against Malware: This course provides staff members with an overview of basic protection against malware. Topics include: the types of malware, how malware works and protective strategies.
Copyright Infringement: This course covers basic knowledge about copyright laws, print and audio materials, visual and multimedia materials, and the internet and digital media.
Cybercriminals have learned that a successful way to take advantage of a victim is through social engineering. We've seen this recently at Citrus College. Social engineering begins with research, whereby an attacker reaches out to a target to gain information and resources.
When someone you don't know contacts you and asks you open-ended questions, this may be the first step of a social-engineering attack. After the attacker reaches out to you, they will then attempt to establish trust with you and get you to provide them with the information or access that they need. Often, the attacker does this by creating a sense of urgency.
One common social-engineering scam is the gift-card scam. The attacker poses as a supervisor or manager (the impersonator). The impersonator will email the victim and begin a brief email exchange. The impersonator will tell the victim that they need to purchase one or more gift cards for other employees but that they are unavailable to do so, and will ask the victim to buy several gift cards and keep one for themselves. As the victim is worried about pleasing the impersonator, the victim goes through with the purchase, spending hundreds or thousands of dollars.
How do you avoid becoming a victim of these types of attacks? Ask yourself if the request makes sense. Check the email address of the sender. Does the sender's email address come from Citrus College? Is there a warning that the e-mail came from outside of the Citrus College e-mail system?
Whenever you receive an "urgent" email communication, the first thing you should do is contact the sender using another mode, such as phone or text message, and confirm that the email is legitimate. If something seems off to you, it probably is.
The Internet is full of data about you. Whenever you play a game, shop, browse websites, or use any of numerous apps, your activity and some of your personal information may be collected and shared.
Similarly, the business of higher education requires us to collect, process, and store the digital information of others. Whenever we handle such information, we need to think about how we want our own information treated and treat other people's data with the same care and respect.
Protect yourself by following these tips:
Protect the information, identity, and privacy of others by following these tips:
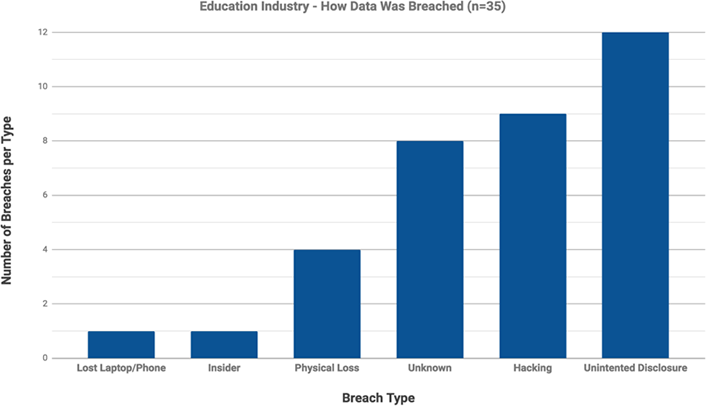
In 2017, nearly eight million records in the education industry were breached in 35 events. More than half of the breaches in the education sector were caused by activities directly attributable to human error, including lost devices, physical loss, and unintended disclosure. These breaches were arguably preventable through basic information security protection safeguards.
All Citrus College staff and faculty have a responsibility to know basic information security protections to safeguard data and prevent those data from being mishandled.
Here are some things you can do every day to protect our student data.
Content for Security Matters is courtesy of the EDUCAUSE Cybersecurity Program.
Shopping, surfing, banking, gaming, and connecting Internet of Things devices such as toasters and refrigerators are some of the many actions performed each minute in cyberspace. These common everyday activities carry the cyber threats of social engineering to gain unauthorized access to data, identity theft, bullying, location tracking, and phishing, to name just a few. How can we decrease our risk from these cyber threats without abandoning our online activities altogether? Here are some basic online tips everyone can follow to help stay secure while online.
Remember that you are in control of your online activities. Following these security tips will give you peace of mind while online.
Monthly content for Security Matters is courtesy of the EDUCAUSE Cybersecurity Program.
With an increasing amount of sensitive data being stored on personal devices, the value and mobility of smartphones, tablets, and laptops make them appealing and easy targets. These simple tips will help you be prepared in case your mobile device is stolen or misplaced.
What can you do if your laptop or mobile device is lost or stolen?
Report the loss or theft to the appropriate authorities. These parties may include representatives from law-enforcement agencies, as well as hotel or conference staff. If your device contained sensitive institutional or student information, immediately report the loss or theft to Technology and Computer Services so that we can respond quickly to the incident.
Monthly content for Security Matters is courtesy of the EDUCAUSE Cybersecurity Program.
Social engineering - manipulating people into doing what they want - is the most common way for cybercriminals to steal information and money. According to an article on Wired.com, between November 2017 and February 2019, six hundred and sixty (660) education-related institutions were targeted with a scam in which employees were tricked into purchasing gift cards and sending the codes to someone they wrongly assumed was a trusted authority.
Social engineering is at the heart of all types of phishing attacks - those conducted via email, SMS, and phone calls. Technology makes these sorts of attacks easy and very low risk for the attacker. Make sure you're on the lookout for these variants on the traditional, mass emailed phishing attack:
No matter the medium, follow these techniques to help prevent getting tricked by these social engineering attacks:
To help you more readily identify suspicious e-mails, our mail server will automatically add a "caution" or warning footer (in a yellow box) at the bottom of any e-mail that is sent from an external source. Take time to reach out to senders via phone or a new e-mail to confirm any unusual action requested of you.
Monthly content for Security Matters is courtesy of the EDUCAUSE Cybersecurity Program.
As you prepare to leave for the winter break, be sure to update your voicemail greeting on your ShoreTel office phone. Follow these steps to update your greeting, change your availability state, change your password, and record your name.
Press – Voicemail key (to the right of the number keys)
You will be asked to enter your password followed by #
For first time access only:
(Main Menu) Press 7 – This option takes you to the mailbox options
To record a personal greeting – Press 1
To set up/change your availability state – Press 2
To change your password – Press 4
Record your name – Press 6
Need help? Contact the IT Help Desk at x 4357 (dial 'HELP') from any campus phone.
October is National Cybersecurity Awareness Month (NCSAM). This is a collaborative effort to ensure everyone has the resources they need to stay safe online. NCSAM is spearheaded by the U.S. Department of Homeland Security and the National Cyber Security Alliance.
It's everyone's job to ensure online safety at work . The lines between our work and daily lives are becoming increasingly blurred, and it is more important than ever to be certain that smart cybersecurity practices carry over between the two. When you are on the job, Citrus College's online security is a shared responsibility.
Here are some simple steps that can make you safer and more secure at work and home:
Keep security software current: Having the latest security software, web browser and operating system is the best defense against viruses, malware and other online threats.
Automate software updates: Many software programs will automatically connect and update to defend against known risks. Turn on automatic updates if that's an available option.
Protect all devices that connect to the Internet: Along with computers, smartphones, gaming systems and other web-enabled devices also need protection from viruses and malware.
Lock down your login: Fortify your online accounts by enabling the strongest authentication tools available, such as biometrics, security keys or a unique one-time code through an app on your mobile device. Your usernames and passwords are not enough to protect key accounts like email, banking and social media.
Make your password a sentence: A strong password is a sentence that is at least 12 characters long. Focus on positive sentences or phrases that you like to think about and are easy to remember (for example, "I love country music."). On many sites, you can even use spaces!
Unique account, unique password: Having separate passwords for every account helps to thwart cybercriminals. At a minimum, separate your work and personal accounts and make sure that your critical accounts have the strongest passwords.
Write it down and keep it safe: Everyone can forget a password. Keep a list that’s stored in a safe, secure place away from your computer. You can alternatively use a service like a password manager to keep track of your passwords.
When in doubt, throw it out: Links in emails, social media posts and online advertising are often how cybercriminals try to steal your personal information. Even if you know the source, if something looks suspicious, delete it.
Get savvy about Wi-Fi hotspots: Limit the type of business you conduct and adjust the security settings on your device to limit who can access your machine.
Protect your $$: When banking and shopping, check to be sure the site is security enabled. Look for web addresses with "https://" or "shttp://", which means the site takes extra measures to help secure your information. "http://" is not secure.
Social engineering is at the heart of all phishing attacks, especially those conducted via e-mail. Technology makes phishing easy. Setting up and operating a phishing attack is fast, inexpensive, and low risk: any cybercriminal with an e-mail address can launch one.
According to Verizon's 2017 Data Breach Investigations Report, the education sector saw a rise in social engineering–based attacks. Students, staff, and faculty all suffered losses when personal data and research were disclosed to unauthorized parties. Phishing played a part in more than 40% of these breaches. Knowing what you're up against can help you be more secure. Here are a few things you can do to guard against phishing attacks:
Monthly Content for Security Matters is courtesy of the Educause Cybersecurity Resources.
What is Ransomware?
Ransomware is a type of malicious software that encrypts your files. Often, the only way to decrypt and gain access to the files is by paying a "ransom" or fee to the attackers. Ransomware may spread to any shared networks or drives to which your devices are connected.
How Can I Get Infected with Ransomware?
Common vectors for ransomware attacks include e-mails with malicious attachments or links to malicious websites. It's also possible to get an infection through instant messaging or texts with malicious links. Antivirus may or may not detect a malicious attachment, so it's important for you to be vigilant.
How Can I Protect Myself Against Ransomware?
There are two steps to protection against ransomware:
Probably the Most Important Steps You Can Take to Prepare
What Do I Do If I Think I'm Infected?
Monthly Content for Security Matters is courtesy of the Educause Cybersecurity Resources.
With the threat of hacking, malware, phishing, and other digital threats constantly looming, it can be easy to overlook the importance of physical security. Here are some ways to improve the security of our technology resources and confidential data by securing our environment.
Monthly Content for Security Matters is courtesy of the Educause Cybersecurity Resources.
Did you know that May 3 was World Password Day?
Your passwords are the key to a host of information about you, and potentially those close to you. If someone can access your personal information, it can have serious long-term effects - and not just online! Follow these recommendations from the World Password Day website to protect your identity while making the Internet more secure for everyone:
Monthly Content for Security Matters is courtesy of the Educause Cybersecurity Resources.
You may be planning a trip during spring break or the summer months. Unfortunately, traveling with devices can mean increased risks for keeping your personal data private as well as the potential for device theft.
Protect your tech and data when traveling
Travel only with the data that you need; look at reducing the amount of digital information that you take with you. This may mean leaving some of your devices at home, using temporary devices, removing personal data from your devices, or shifting your data to a secure cloud service. Authorities or criminals can't search what you don't have.
You may decide that inconvenience overrides risk and travel with electronic devices anyway. If this is the case, focus on protecting the information that you take with you. One of the best ways to do this is to use encryption. Make sure to fully encrypt your device and make a full backup of the data that you leave at home.
Get your device travel ready
These guidelines are not foolproof, but security experts say every additional measure taken can help reduce the chances of cyber theft. Monthly Content for Security Matters is courtesy of the Educause Cybersecurity Resources.
"The Internet is a powerful and useful tool, but in the same way that you shouldn't drive without buckling your seat belt or ride a bike without a helmet, you shouldn't venture online without taking some basic precautions."
This is an important reminder from the National Cyber Security Alliance that cybersecurity is everyone's responsibility as an individual and a member of our ever-growing online community. Here are some tips to keep in mind as we work together to create a better, safer digital world for ourselves and others.
Monthly content for Security Matters is courtesy of the Educause Cybersecurity Resources.
January 28, 2018 is Data Privacy Day. This event is held each year and is led by the National Cyber Security Alliance (NCSA) in commemoration of the signing of the first legally binding international treaty dealing with privacy and data protection.
Everyone in our community is responsible for the protection of the privacy and personal information of our students and employees. Recommended best practices to ensure adequate protection of district restricted or sensitive information is described in Citrus College Administrative Procedure (AP) 3724. These recommendations are listed as follows: